David Webb, Managing Director at Valkyrie, who served 26 years in the UK Military, delves into why applying military principles to client problem-solving can be a useful tool, especially regarding security.
In the military, orders are clear, short, and direct—especially at the highest level: “secure a location,” “protect a key asset,” or “gather intelligence.” These commands, while seemingly straightforward, are supported by layers of strategic, operational, and tactical planning. In the civilian world, particularly in high-stakes security, the requests can be similarly broad or unspecified. A high-net-worth individual might say, “I want to be more secure,” or “secure my home.” While these requests appear simple on the surface, they carry with them a host of implied tasks that must be addressed through a structured and nuanced approach. This is where the principles of strategic, operational, and tactical planning come into play, ensuring that every aspect of the problem is analysed and addressed. As you break down the high-level request, a cascade of detailed tasks follows, particularly at the tactical (implementation) level.
From Vision to Implementation: Strategic Planning in Security
The strategic level of planning in the military focuses on the broader mission. It sets the direction, the end goal, and the overarching objectives. In security terms, this is akin to understanding the client, their lifestyle, environment, and specific concerns. What drives their request for greater security? Are they concerned about physical intrusion, a digital breach, or a combination of both? It is important to go beyond their initial request, to understand what is motivating them, and to make sure your actions align with their ultimate goals.
For example, a high-net-worth client may want to secure a property they visit infrequently, meaning the security strategy needs to account for remote monitoring, adaptable responses, and advanced surveillance systems. The first step is always understanding the client’s objectives, much like a general must understand the desired outcome of a military campaign before making any decisions.
At this level, security planning involves assessing risk holistically—evaluating the client’s public profile, the property layout, and potential vulnerabilities in both the physical and digital realms. Whether protecting a townhouse in Mayfair or a secluded country estate, strategic security planning is designed to protect the individual, their assets, and their reputation, aligning every element of the plan with the client’s unique needs.
Operational Planning: Bridging Strategy and Execution
Once the objective is defined and a strategy is in place, operational planning turns those broad goals into actionable steps. This stage mirrors military operational planning, where decisions about resource deployment and logistics are made to carry out the mission.
In the context of securing a high-net-worth individual’s home, operational planning could include determining the types of surveillance systems to install, how physical security measures like fences or gates should be configured, and how cybersecurity measures will protect the home network and digital devices. For a client deeply embedded in public life or social media, this might also involve protecting their online presence, limiting the amount of personal information available to the public, and shielding them from digital threats, like hacking or cyber harassment. It may also involve awareness training around the evolving threat landscape and how to identify threats, such as phishing emails.
In this phase, it’s important that all aspects of security work in harmony. Physical and digital measures must be interconnected—installing the most sophisticated physical barriers while leaving cyber vulnerabilities exposed would be akin to securing a fortress with open gates. The same principle applies to internal coordination: just as military operations require communication between air, land, and naval forces, a client’s physical and cyber security teams must work together seamlessly.
Tactical Implementation: On-the-Ground Execution
The tactical level is where security systems are executed and maintained. In the military, this is the on-the-ground phase where plans are put into action by the soldiers who carry out the strategy and operations. In the civilian world of high-end security, this is where the day-to-day management and execution of security systems occur.
For example, once a client’s estate is secured with advanced surveillance systems, biometric access control, and cybersecurity measures, the tactical level involves the continuous monitoring and updating of those systems. This might include regular security audits, testing of alarm systems, penetration testing for cybersecurity, and even simulating breaches to ensure every system is functioning optimally. This ongoing support is vital to maintaining the security infrastructure against evolving threats and the client’s own personal circumstances.
It’s here, at the tactical level, where technology plays a crucial role. The rise of smart homes, Internet of Things (IoT) devices, and integrated security systems has transformed how high-end security is managed. Biometric locks, AI-enhanced surveillance cameras, and smart sensors that detect unusual activity are just a few examples of how technology enables a more seamless and reliable security experience. But as with any high-tech solution, these systems must be maintained and updated regularly to stay ahead of evolving threats.
Cybersecurity: Protecting the Digital Frontier
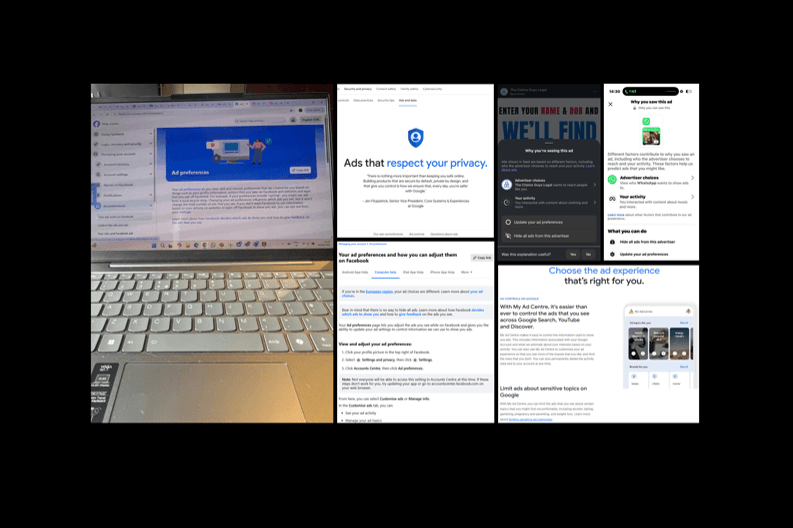
The digital age has expanded the scope of what it means to secure a home or personal space. In today’s world, securing the physical space is no longer enough; a client’s online presence is equally vulnerable. Cyber threats—ranging from hacking attempts to ransomware attacks—can cause just as much damage, if not more, than a physical intrusion. Social media accounts can be breached, personal information exposed, or smart home devices hacked, compromising the client’s reputation or data.
Cybersecurity forms an integral part of the strategic, operational, and tactical planning for high-end clients. At the strategic level, it involves assessing the digital landscape: what data is being shared, how devices are connected, and where vulnerabilities might lie. Operationally, this could mean installing firewalls, employing encryption protocols, and managing network access to ensure all digital entry points are protected. Tactically, it’s about staying vigilant—monitoring for breaches, responding to suspicious activity, and regularly updating software to patch vulnerabilities. This again involves educating clients on the threats and how to recognise them.
One common oversight is the risk posed by social media. Many high-net-worth individuals maintain an active online presence, and even seemingly innocuous posts can reveal valuable information about their whereabouts, routines, or possessions. Cybersecurity measures must include guidelines for safe social media use, ensuring that clients are protected not only by technology but by thoughtful digital behaviour.
Intelligence: Anticipating and Preventing Threats
In both military and civilian contexts, intelligence plays a key role in preventing threats before they materialise. In the world of high-net-worth security, intelligence might involve monitoring for emerging threats, identifying potential adversaries, or tracking online chatter that could indicate a heightened risk.
Private security firms, much like military operations, must stay ahead of the curve by continually gathering intelligence. This could mean monitoring the dark web for signs of impending cyber-attacks or using open-source intelligence (OSINT) to track developments in the client’s environment. Whether it’s a potential protest outside a client’s property or an increase in online threats, intelligence allows for proactive responses, rather than reactive damage control.
Harmonising All Aspects: The Synergy of Comprehensive Security
Much like a well-coordinated military campaign, the success of any security plan relies on synergy between its strategic, operational, and tactical components. Each element must be aligned to ensure the client is fully protected across all fronts—whether it’s their physical residence, digital assets, or personal profile.
In the same way that military forces must coordinate air, land, and sea operations to achieve their objectives, all elements of a security plan must work together. This requires clear communication between the client and the security team, a deep understanding of the unique threats they face, and a dynamic approach that evolves as the risk landscape changes. This is why it is essential to know the team undertaking the work and to ensure they are working towards a clear, defined objective.
The same strategic framework—aligning vision with execution—is not only relevant to security but can be applied to all forms of project management, whether overseeing building work, managing large-scale events, or handling complex personal projects. By harmonising all aspects, from planning to implementation, any undertaking becomes more robust and efficient, delivering results that are comprehensive and well-coordinated.
Ultimately, success lies in understanding the big picture while executing with precision at every level, because tactical failure can have far-reaching strategic consequences.
Applying military principles – Health & Wellness Featured Stories By Admin Contributor (tatler.com)